Onion routing is a key component of the Bitcoin Lightning Network's safe, confidential, and effective payment routing.
In this article i explores the complex mechanisms of onion routing in the Lightning Network and offers thorough explanations supported by useful examples.
By the end of the article, you will have a thorough grasp of how onion routing enables safe transactions on the Lightning Network, covering everything from source-based routing to HTLCs and key generation.
With the development of the Bitcoin Lightning Network, Bitcoin's scalability issues have been significantly resolved, allowing for quick and affordable transactions via off-chain payment channels.
The Lightning Network’s protocol to transmit payments is described in BOLT #4, and is often called “Onion Routing Protocol”.
Fundamentals of Onion Routing
Onion routing, a privacy-preserving method taken from the Tor network, is at the core of the Lightning Network.
Onion routing works using the idea of layered encryption, in which the sender of a message encodes data in successive layers of encryption. Every network intermediary node removes a layer of encryption, exposing only the data required to send the message to the subsequent hop.
Alice wants to use the Lightning Network to send Dina a payment. Alice creates an onion packet with encrypted hop payloads in order to protect privacy.
She then constructs the "onion". She works backwards, starting with Dina first. She locks a container addressed to Dina with a key that only Alice and Dina have, concealing the cash within. She now picks up the container, places it into an other container meant for Chan, and locks it using a key that only Alice and Chan are in possession of. She treats Bob in the same way.
Source-Based Routing
This feature of the Lightning Network allows the sender of the payment to ascertain the path the payment packet takes.
In contrast to destination-based routing, which is used in standard internet routing, source-based routing improves privacy by hiding the sender and recipient of a transaction.
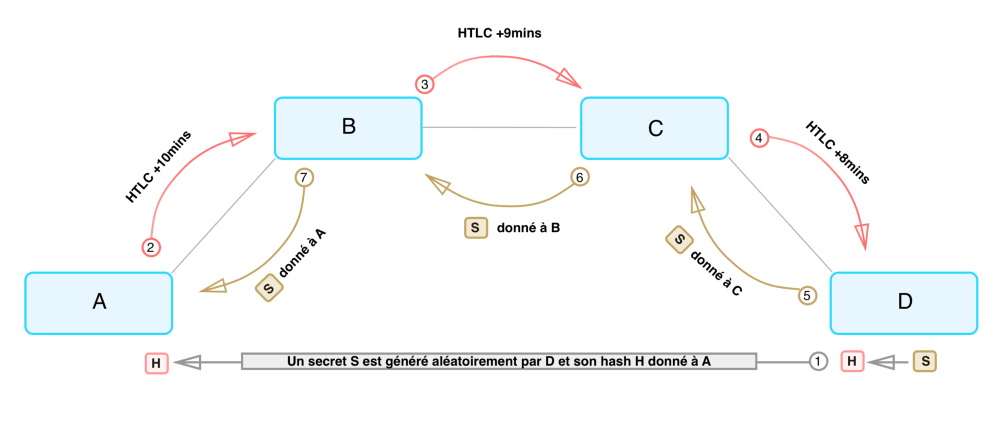
Example: Alice chooses the payment path from her node to Dina's node as the payment sender.
Alice determines each hop along the way, thus intermediate nodes only see what comes before and after them. The Lightning Network's anonymity is strengthened by this source-based routing technique, which keeps transaction data hidden from prying eyes.
HTLCs and Onion Routing
Hash Time Locked Contracts, or HTLCs, are essential to the Lightning Network's onion routing system for processing payments. HTLCs use cryptographic primitives like timelocks and hash functions to provide safe, trustless transactions.
Each hop needs the following to put up an appropriate HTLC:
The sum to be forwarded.
The payment's confidentiality.
The payment channel ID to which the onion should be sent.
The timelock that is being sent out.
The majority of this data is derived from the "channel update" message, which includes details on timelock requirements, routing fees, and the payment channel ID. The payment secret is computed and included in Dina's payment invoice. The amount to transfer is the total amount plus the fees accrued for each hop.

Key Generation and Shared Secrets
The Lightning Network's onion routing is based on key generation and shared secrets. Nodes obtain shared secrets through Elliptic Curve Diffie–Hellman (ECDH) key exchange, which permits deterministic session key randomization at each hop.
A value that can be independently produced by Alice and the intermediary node using their respective private and public keys is referred to as the shared secret.
Shared secrets are essential to onion routing because they allow Alice to obtain the same keys from each intermediate. Alice then uses these keys to prepare and hide the onion layer, and the middleman uses them to interpret it.
Conclusion
The Bitcoin Lightning Network relies heavily on onion routing for safe, discrete, and effective payment routing. Developers, researchers, and users can use onion routing's ability to foster innovation and adoption in the Lightning ecosystem by grasping its technical nuances. Onion routing appears as a crucial element in achieving the Lightning Network's maximum potential, with real-world examples demonstrating its useful applications.
Reference
https://lnbook.256k1.dev/#onion_routing
https://voltage.cloud/blog/lightning-network-faq/what-is-onion-routing-how-does-it-work/
https://github.com/lightning/bolts/blob/master/11-payment-encoding.md